
How to create an effective healthcare compliance program in 2020
Contrary to popular belief, healthcare compliance rules and regulations are not only about patient data. They also play a vital role in ensuring that patients

Contrary to popular belief, healthcare compliance rules and regulations are not only about patient data. They also play a vital role in ensuring that patients

Data security remains a hot topic among enterprises across all industries. This is because many companies still need consumers’ personal data to improve customer experience

If a fire or a data breach struck your small business tomorrow, would you know what to do? If your place of business was leveled

Businesses, from healthcare to finance to retail to manufacturing, must all comply with data security and privacy regulations. Not only is compliance mandatory, but it

Material requirement planning (MRP) has, for the past 30 years, been helping manufacturers deal with production planning, scheduling, and inventory control. It has become an

With digital technology having such an immense impact on how people work, the old methods of handling tax reports and other accounting data are no
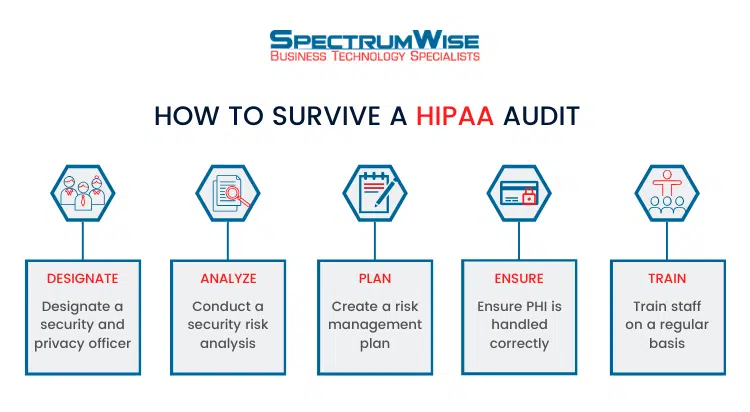
Just as healthcare data has become very valuable to cybercriminals, compliance with the regulations of the Health Insurance Portability and Accountability Act of 1996 (HIPAA)

Cybersecurity has become essential for any real estate business that seeks to thrive or survive. When your real estate firm’s data, network, and systems are

They say that every business is a technology company. What is being said is that every successful business employs technology to its advantage. Businesses that

Disruption in the manufacturing industry has become more significant because of technological advancements like the Internet of Things (IoT), the cloud, and artificial intelligence (AI).
"*" indicates required fields